Kestrel on Windows
Seq uses Windows built-in HTTP.sys web server by default. The Kestrel web server is an alternative with better support for some modern web technologies, including the HTTP features required for OTLP/gRPC service hosting.
Kestrel is the default and only supported web server option when hosting Seq on Linux, and has been used in this role since the Seq 5.0 release in 2018.
Feature differences
This section compares Seq hosted under Kestrel with Seq under HTTP.sys. It's not exhaustive, but should point out what you can expect to gain and lose by enabling Kestrel instead of HTTP.sys.
✅ Enabled by Kestrel
- OTLP/gRPC ingestion is enabled (HTTPS only)
- TLS certificates may be loaded from the
Certificates\storage folder in PFX or PEM format as on Linux
⛔ Unsupported with Kestrel
- Windows Integrated Authentication via NTLM/Kerberos/Negotiate is unsupported (Active Directory authentication remains supported, but users must supply a username and password to the Seq login screen)
seq bind-sslis unsupported; this command configures HTTP.sys (see below for TLS configuration instructions for Kestrel)- SNI is unsupported
- Hosting Seq under a "virtual directory" path is unsupported
- Only one Seq instance can listen on each port
- Incoming requests will not be filtered by hostname
Enabling Kestrel
At install time or by running Seq Service Administration
The Seq Service Administration wizard supports configuring Kestrel via the "configure Kestrel instead" hyperlink beneath the Listen URI text field:
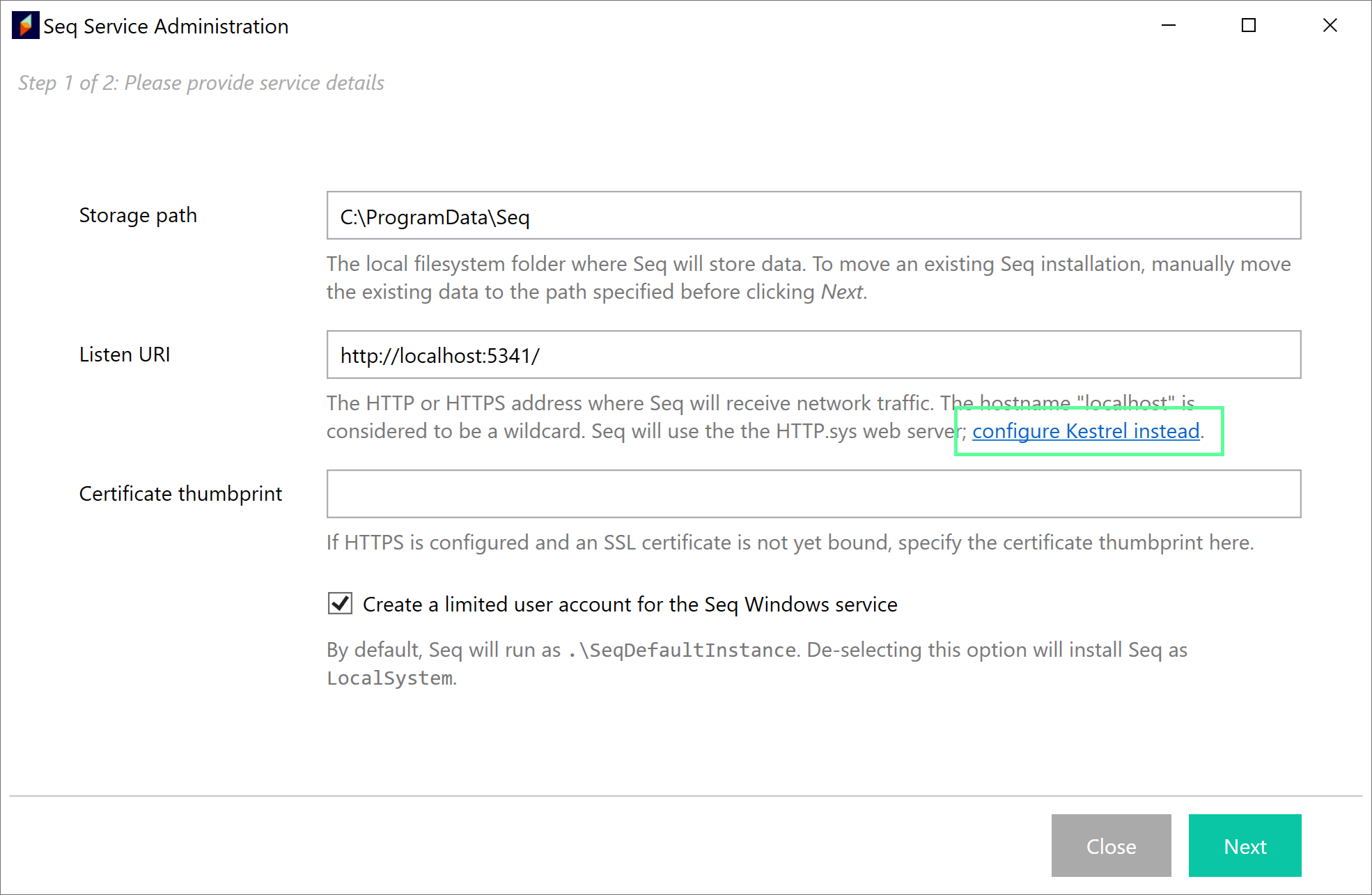
Seq Service Administration wizard, Listen URI configuration field showing "configure Kestrel instead" link in help text.
Selecting "configure Kestrel instead" will modify the available options and fully configure Kestrel on completion of the wizard.
The wizard can be found under the Windows Start menu.
At the command line
From an administrative PowerShell prompt:
seq config set -k api.webServer -v Kestrel
seq service restartHowever, be careful to check the api.listenUris setting to ensure that Seq listens at most once at each port. If multiple api.listenUris entries exist for the same port, Seq will fail to start. Use the seq config commands to show and manipulate this setting.
See also the section on TLS configuration immediately below.
TLS configuration
When hosting Seq under Kestrel on Windows, Seq searches the Local Computer\Personal certificate store for SSL certificates that:
- Match the hostname portion of the HTTPS URI Seq is configured to serve traffic for; e.g. if
https://seq.example.comis configured in the installation wizard, Seq will look for a certificate with subjectCN=seq.example.com("Issued to"seq.example.com), and - That include a private key.
The Seq service account also needs appropriate permissions to read these certificates; this is set automatically by the Seq Service Administration tool/install wizard, but will have to be manually applied if configuring Seq via the command-line.
To check or add these permissions, find the certificate in certlm.msc:
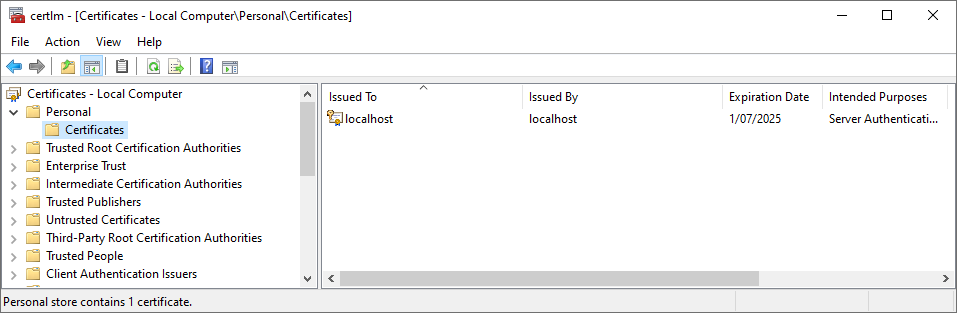
Then, right click on the certificate, select All Tasks, Manage Private Keys..., and add the SeqDefaultInstance service account (or other service account used by Seq) with full control to the permissions associated with the certificate.
Switching back to HTTP.sys
If for any reason you need to switch Seq from Kestrel to HTTP.sys, the best approach is to reconfigure Seq by running Seq Service Administration from the Windows Start menu, and leaving the default HTTP.sys web server configuration selected.
To switch back manually, at an administrative PowerShell prompt run:
seq config clear -k api.webServer
seq service restartYou may need to consult the logs in C:\ProgramData\Seq\Logs to diagnose any problems arising from differences in configuration.
Updated 5 months ago
