Microsoft Entra ID Authentication
Instructions for setting up Microsoft Entra ID (formerly Azure Active Directory) authentication with Seq
Seq can authenticate users in Microsoft Microsoft Entra ID. This makes it easier for organizations to centrally manage user accounts.
When this configuration is enabled, users will be redirected to an external Microsoft Entra ID sign-in page to authenticate when logging into Seq.
Before you begin...
Popular browsers, including Chrome, will no longer send cross-site authentication cookies unless the request is secure (HTTPS).
You will need to configure Seq with an SSL certificate (Windows) (Docker) before setting up Microsoft Entra ID authentication.
If Seq is behind a proxy or load balancer, you must also set
SEQ_API_CANONICALURIto the public URL you use to access Seq (Docker), or runseq config set -k api.canonicalUri -v <your Seq URL>and restart the Seq service (Windows).
Generate a Recovery Key
See the Recovery Keys topic for instructions for generating a recovery key, which can be used to easily reset authentication or update an expired client secret if access to the Seq UI is lost.
Getting started
The first step to enable Microsoft Entra ID authentication in Seq is to open Settings > System and choose Enable Authentication.
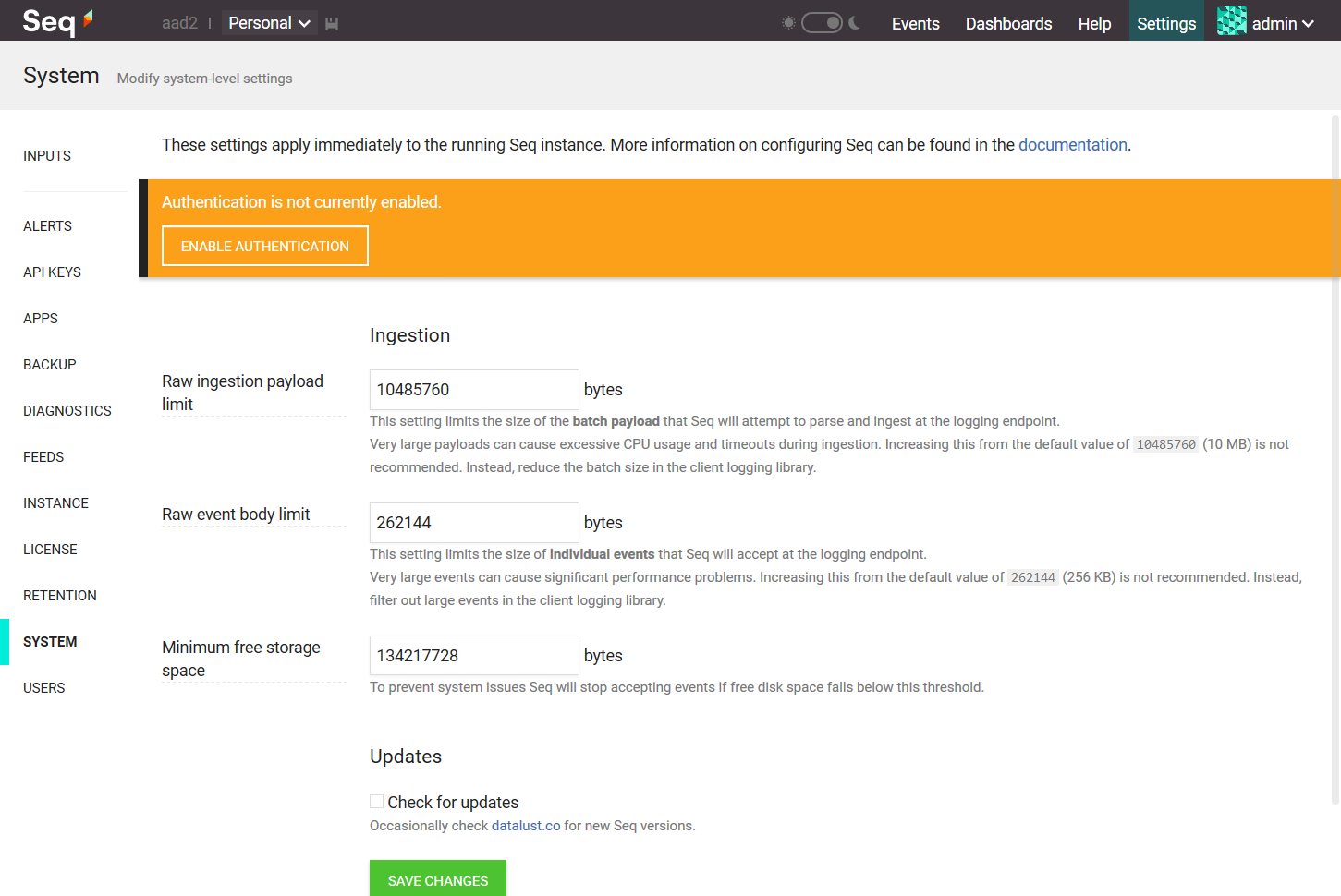
If you've already enabled a different authentication provider, click Change beside the authentication provider edit box.
Preserving Existing User Accounts
If you have existing user accounts that you want to link and continue using with AAD, please contact Support for migration assistance.
Seq will load the Enable Authentication screen.
Choose Microsoft Entra ID from the Authentication Provider drop-down. This will show some edit boxes for the various pieces of information we'll collect from the Azure Portal.
Registering Seq as an application in Azure Portal
In the App registrations screen, choose New app registration:
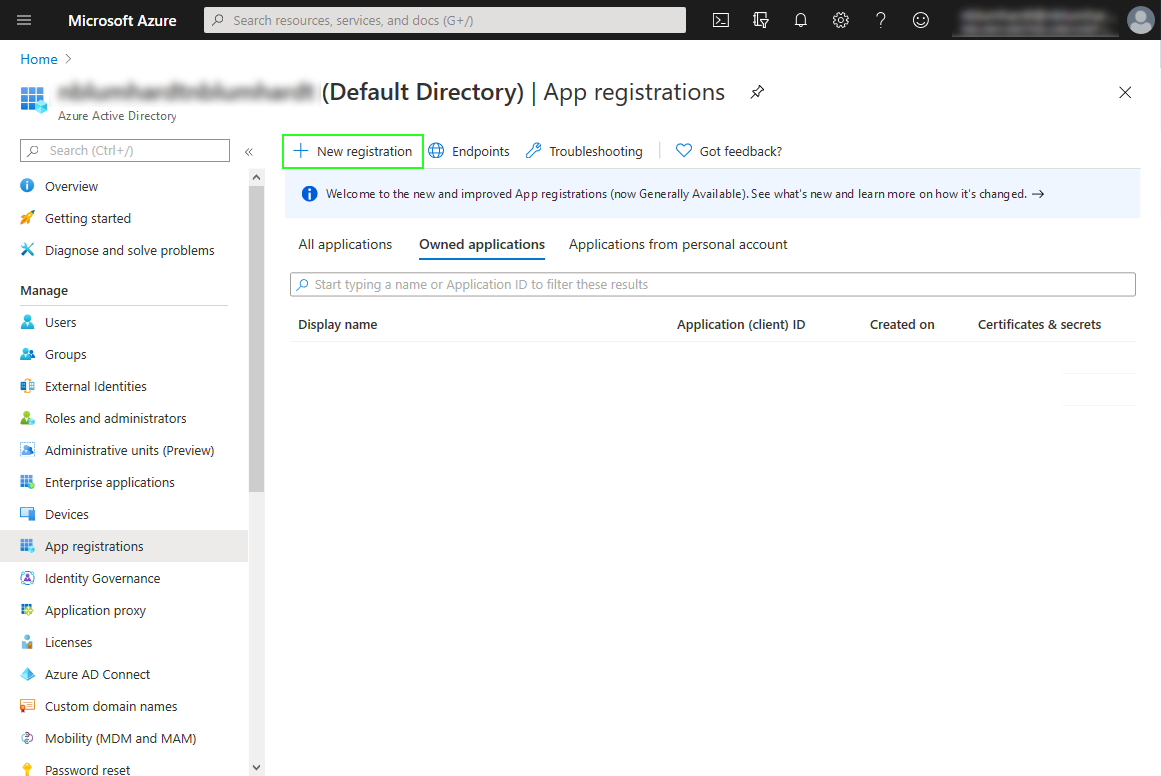
You can call the application anything you like that will help you to identify it.
Although the heading states that the redirect URI is optional, you must add the address of your Seq instance, with /aad appended, here:
This will show the application's identifiers. Copy the Application ID and Directory ID values into the corresponding fields in Seq:
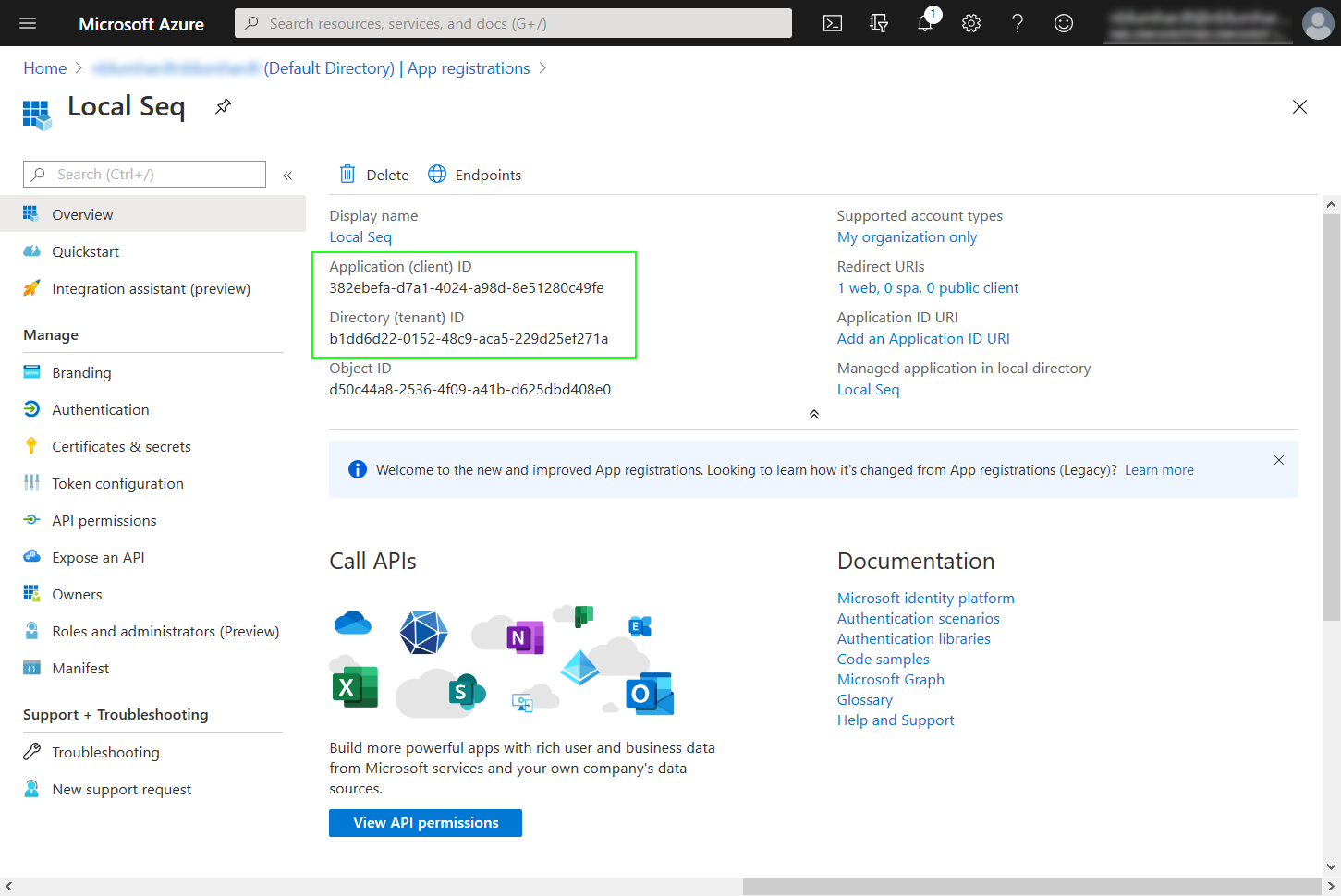
Under Certificates and Secrets, create a new client secret and copy it into the corresponding field in Seq:
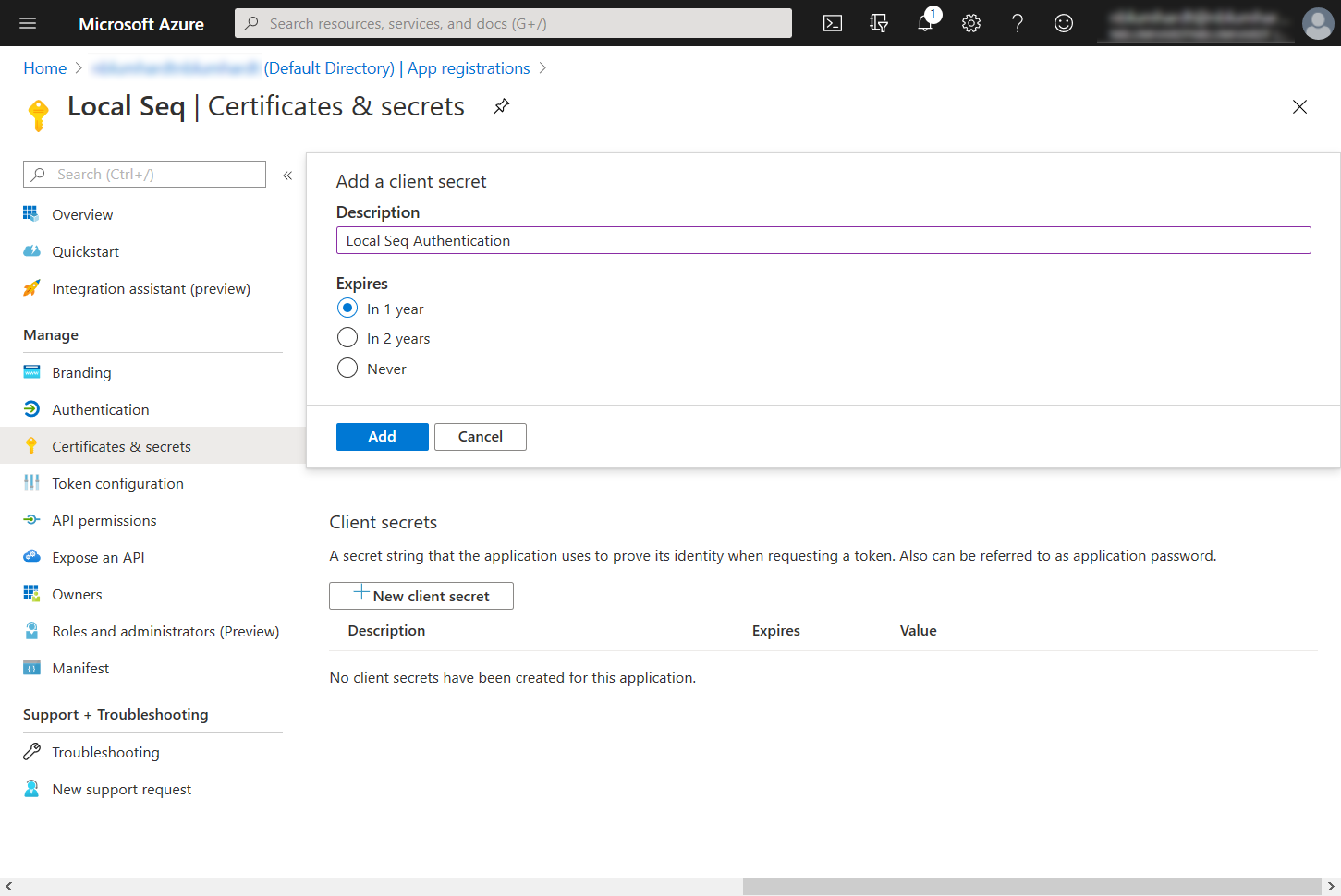
Your Enable Authentication screen in Seq should now look like:
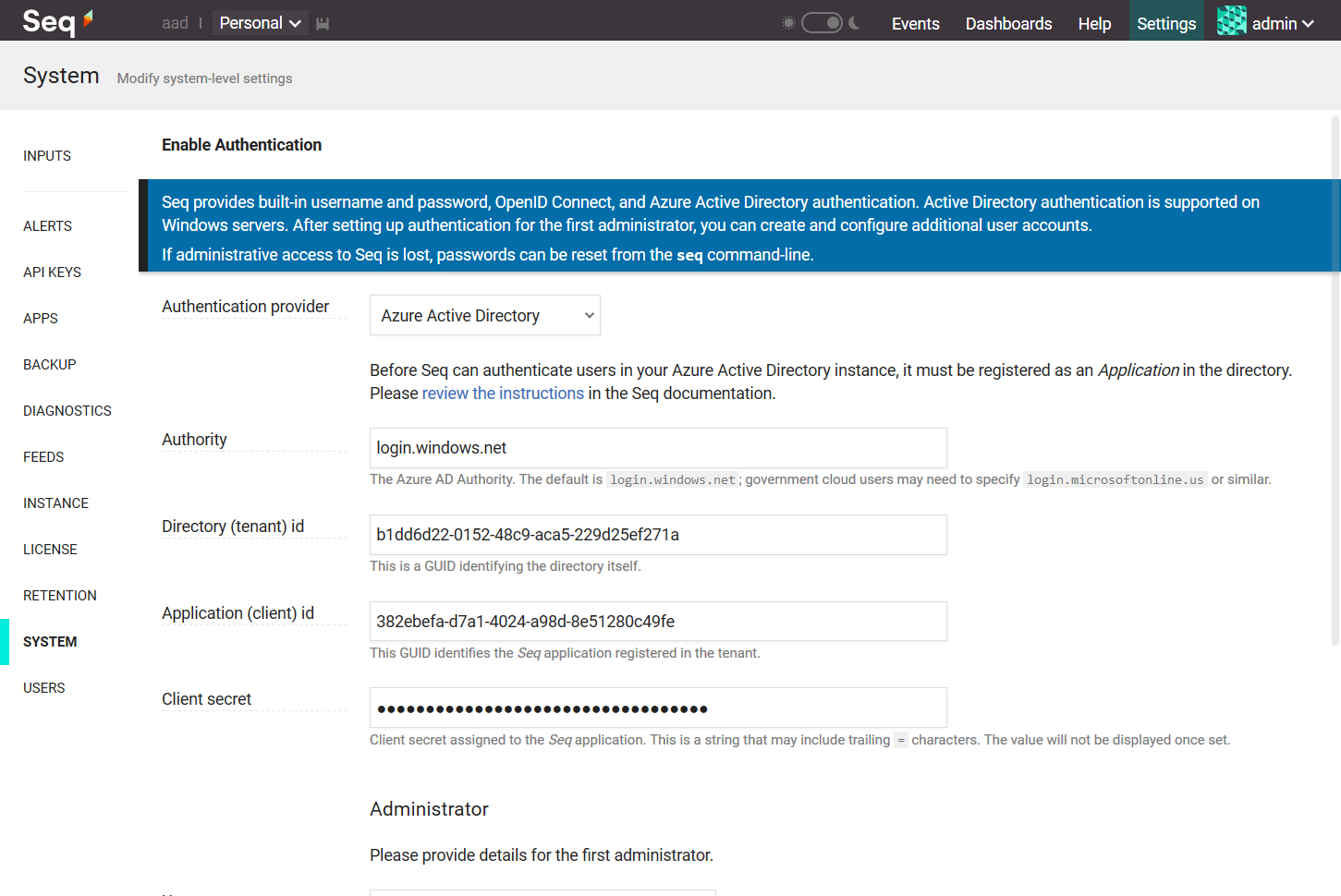
Finally, set the Administrator Username field in Seq to the email address of a user in the directory, and click Enable:
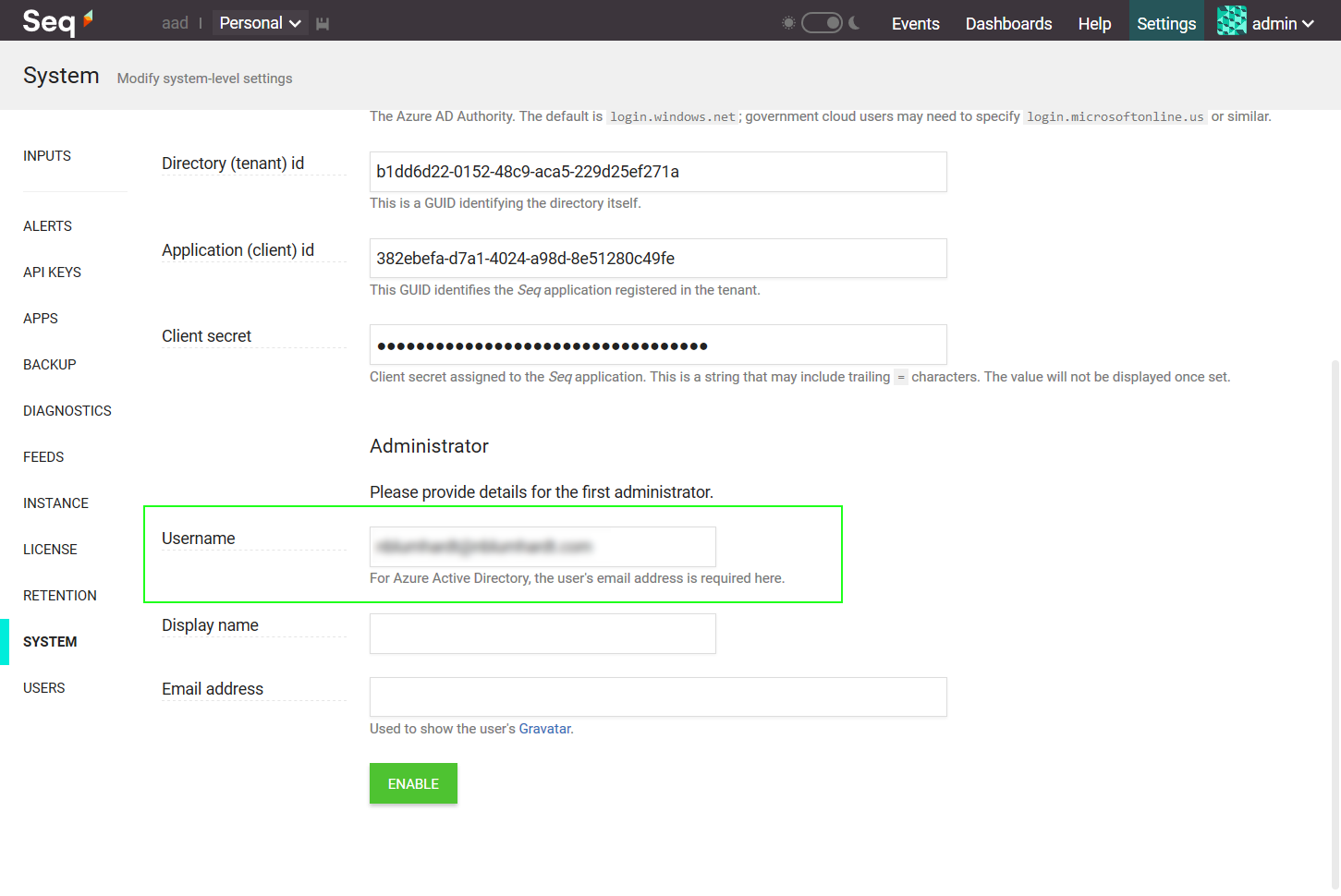
You'll be logged out of Seq, and should be presented with the Seq login screen:

When you click Log in using Microsoft Entra ID, you'll be asked to give the application access to your account information.
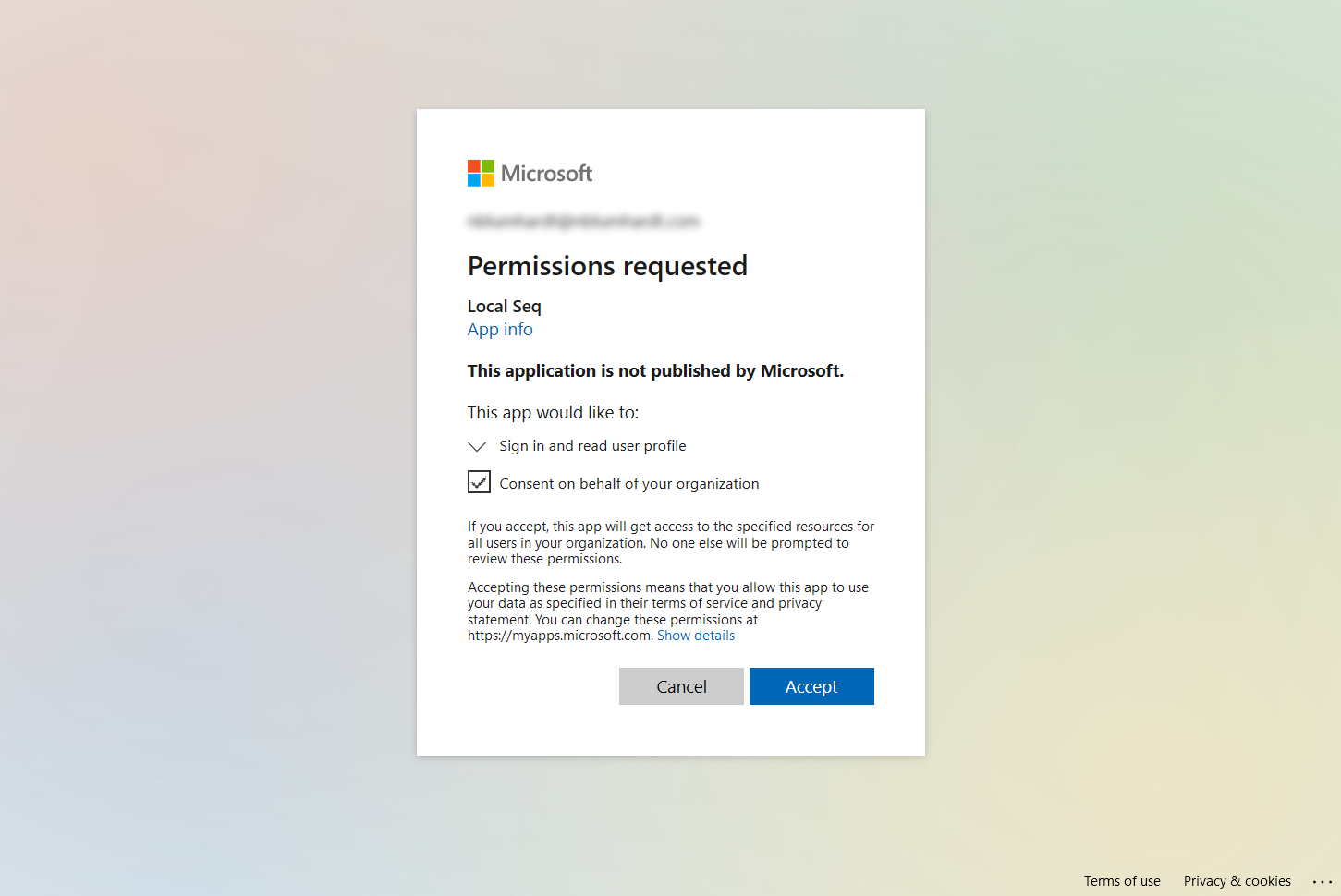
You'll be redirected back to Seq, logged in as the admin user.
If you lose access...
Microsoft Entra ID configuration can sometimes be tricky. If you made a mistake in the final step, see Recovering from Broken Authentication Settings for recovery instructions.
Adding users
Choose Automatically-provision user-level access on the Settings > System screen to automatically create a user-level account for any user who is able to authenticate with the directory.
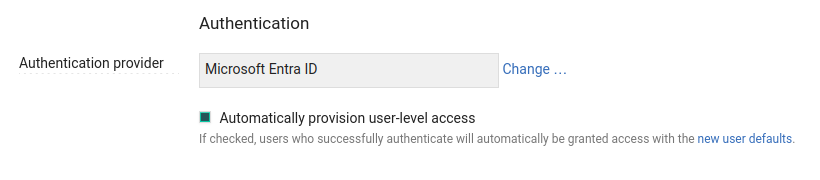
Otherwise, you can add users via Settings > Users as required.
When adding users to Seq, the username for the user must be the email address that's used when logging in to Entra ID.
Troubleshooting
- If Seq generates incorrect login redirects, set the
SEQ_API_CANONICALURIenvironment variable (Docker), orapi.canonicalUrisetting (usingseq config set, on Windows), is set to the full public URL you use to access Seq, including its scheme (HTTPS), hostname, and port.
Updated 5 months ago
